Conclusion: The ability to pay with credit cards on the internet has ushered in a new era of convenience and accessibility in financial transactions. By understanding the benefits of this method, adhering to security practices, and staying informed about the evolving landscape of online payments, individuals can confidently embrace the digital future while ensuring their financial safety. Cybercriminals deploy various techniques to compromise digital transactions, posing risks to both consumers and businesses engaged in online commerce.
Understanding Cyber Card Hacks: A cyber card hack involves the unauthorized access, manipulation, or theft of sensitive payment card information for fraudulent purposes. In a world where scams and crimes are constantly evolving, knowledge is your best defense. By staying informed, practicing caution in online interactions, and sharing information with others, you can contribute to a safer digital environment for yourself and those around you.
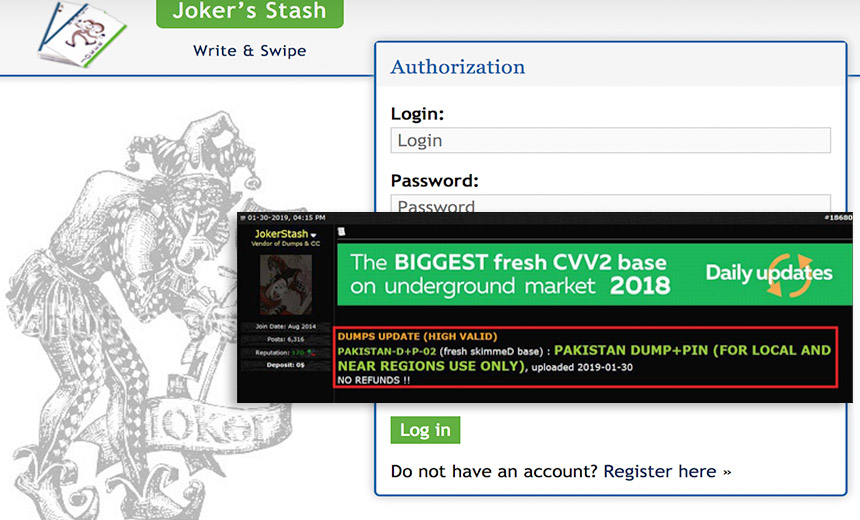
These elements are often used to facilitate unauthorized financial transactions, leading to financial losses for victims. Understanding Card Dumps Track 1&2 with PIN: Card dumps with Track 1&2 data and PIN information involve stealing and trafficking sensitive payment card information, including the magnetic stripe data (Track 1&2) and the associated personal identification number (PIN). Phishing emails, deceptive phone calls, and impersonation are some of the tactics they employ.
 Social Engineering: Thief hackers are adept at exploiting human psychology to manipulate victims into divulging confidential information. Embracing the Future of Transactions: Paying with credit cards on the internet has not only reshaped the way we shop but has also propelled the growth of e-commerce and digital business models.
Social Engineering: Thief hackers are adept at exploiting human psychology to manipulate victims into divulging confidential information. Embracing the Future of Transactions: Paying with credit cards on the internet has not only reshaped the way we shop but has also propelled the growth of e-commerce and digital business models.
Understanding Cyber Card Hacks: A cyber card hack involves the unauthorized access, manipulation, or theft of sensitive payment card information for fraudulent purposes. In a world where scams and crimes are constantly evolving, knowledge is your best defense. By staying informed, practicing caution in online interactions, and sharing information with others, you can contribute to a safer digital environment for yourself and those around you.
These elements are often used to facilitate unauthorized financial transactions, leading to financial losses for victims. Understanding Card Dumps Track 1&2 with PIN: Card dumps with Track 1&2 data and PIN information involve stealing and trafficking sensitive payment card information, including the magnetic stripe data (Track 1&2) and the associated personal identification number (PIN). Phishing emails, deceptive phone calls, and impersonation are some of the tactics they employ.
 Social Engineering: Thief hackers are adept at exploiting human psychology to manipulate victims into divulging confidential information. Embracing the Future of Transactions: Paying with credit cards on the internet has not only reshaped the way we shop but has also propelled the growth of e-commerce and digital business models.
Social Engineering: Thief hackers are adept at exploiting human psychology to manipulate victims into divulging confidential information. Embracing the Future of Transactions: Paying with credit cards on the internet has not only reshaped the way we shop but has also propelled the growth of e-commerce and digital business models.

